Hi folks,
I’m not an aviator, and the closest I’ve come to being a pilot was spending many hours playing Star Wars: X-Wing in the mid-nineties.
Yes, that was cutting edge graphics at the time and, yes, it was glorious.
Anyhow, so I’m not a pilot (in this galaxy), but I understand that there’s this concept called “crabbing”. The deal is essentially this – if you’re flying from point A to point B and there’s no crosswind, then you can basically just point the plane in a straight line and you’ll make your destination. But if there’s any sort of crosswind, you’ll be pushed off course, and you’ll need to periodically course correct in order to make your destination.
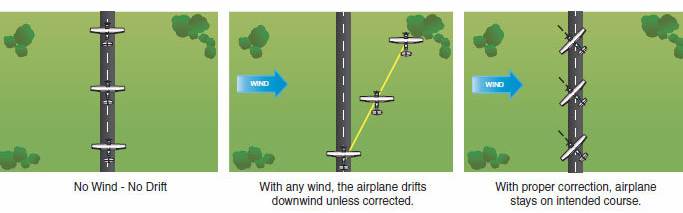
Makes sense, right? And since, I imagine, most flights encounter some amount of crosswinds, corrections are constantly needed.
There are obvious metaphorical applications to life here as well. The most elegant expression of which was probably articulated by Victor Frankl. Any attempt of mine to capture his message will be totally inadequate, so I’ll just point you to him:
https://www.ted.com/talks/viktor_frankl_youth_in_search_of_meaning
At the risk of polluting the purity of Frankl’s message by applying to our context, it also has a very real application to the workplace. At work we often encounter our own crosswinds – very rarely can we march down a clear path towards our destination without encountering resistance, well-intentioned or otherwise. And for that reason, we must be willing to aim beyond our expectations and constantly course correct. It’s only by aiming beyond our perception of the possible that we’re able to achieve our potential.

Although…

Rex